In today’s digital world, our personal information and online activities are constantly under threat. Cybercriminals are constantly developing new ways to exploit weaknesses in our defenses. But fear not! Just like a strong army needs regular drills to stay prepared, your digital security can be significantly improved through a process called security testing.
This blog post will delve into the world of security testing, explaining how it works and why it’s a crucial element in improving your cyber security with security testing. Kyanon Digital will explore different types of security tests, the benefits they offer, and how you can leverage them to build a stronger defense against cyberattacks.
1. What is security testing?
Think of security testing as a checkup for your computer systems. It helps identify potential security gaps – like weak passwords or outdated software – that attackers might exploit. By addressing these vulnerabilities, security testing keeps your systems safe from unauthorized access and other security risks.

2. Why Security Testing is Crucial
In today’s digital landscape, where cyberattacks are constantly evolving, having a robust defense system is no longer optional. Security testing acts as the cornerstone of this defense, proactively identifying and patching vulnerabilities in your systems before attackers can exploit them. Here’s why security testing is crucial:
- Unveiling Hidden Weaknesses: Just like a house with a weak foundation, a system with security vulnerabilities is vulnerable to collapse. Security testing acts as a meticulous inspection, uncovering these vulnerabilities before they can be used by attackers to gain unauthorized access or steal sensitive data.
- Preventing Costly Breaches: Data breaches can be devastating, leading to financial losses, reputational damage, and even legal repercussions. Security testing helps prevent these breaches by identifying and fixing vulnerabilities before attackers can launch their assault.
- Building Trust and Confidence: When your systems are demonstrably secure, it fosters trust with your customers and partners. They know their data is safeguarded, allowing them to interact with your systems with confidence.
- Staying Ahead of the Curve: Cybercriminals are constantly developing new attack methods. Security testing helps you stay ahead of the curve by identifying emerging vulnerabilities and allowing you to patch them before they become a major security risk.
- Continuous Improvement: Security testing isn’t a one-time fix. It’s an ongoing process that ensures your defenses remain strong as your systems evolve and new threats emerge.

3. A Look at Different Security Testing Methods
There are many different types of security testing, each with its own strengths and applications. Here’s a breakdown of some common types:
- Vulnerability Scanning: This automated approach uses tools to scan systems and applications for known weaknesses. It’s efficient for identifying common vulnerabilities but may miss more complex ones.
- Penetration Testing (Ethical Hacking): This involves simulating real-world attacks by ethical hackers who attempt to exploit vulnerabilities and gain unauthorized access. It’s a more in-depth approach that can uncover complex vulnerabilities but requires skilled professionals.
- Security Code Review: This involves manually reviewing code by security experts to identify security flaws like coding errors or weak password hashing practices. It’s particularly useful for catching vulnerabilities early in the development process.

Types based on Testing Focus:
- Web Application Security Testing (WAST): Focuses on identifying vulnerabilities in web applications specifically.
- API Security Testing: Targets vulnerabilities in application programming interfaces (APIs) that connect different applications.
Other Types:
- Risk Assessment: Analyzes your systems and data to identify potential security risks and prioritize mitigation efforts.
- Security Posture Assessment: Evaluates your overall security posture, including security policies, procedures, and controls.
The best approach often involves a combination of these testing methods. Choosing the right type depends on your specific needs, resources, and risk tolerance.
4. What is network security testing?
Network security testing is a specific type of security testing that focuses on the overall security of your computer network. While other security tests might target individual applications or code, network security testing looks at the big picture: firewalls, routers, access points, and how they work together to secure your network from unauthorized access and other threats. Here’s a breakdown of what network security testing entails:
- Focus: Network security testing evaluates the strength of your network’s defenses against intruders and vulnerabilities that could be exploited to gain access to your systems or data.
- Techniques: This testing can involve a variety of techniques, including:
+ Vulnerability scanning: Automated tools scan your network devices for known weaknesses in software, firmware, or configurations.
+ Penetration testing: Ethical hackers simulate cyberattacks to see if they can exploit vulnerabilities and gain unauthorized access to your network.
+ Wireless network testing: This focuses on securing your Wi-Fi network, identifying weak encryption protocols or unauthorized access points that could be exploited by attackers.
- Benefits: By proactively identifying weaknesses in your network defenses, you can take steps to mitigate them before attackers can exploit them. This helps to:
+ Prevent data breaches and unauthorized access to sensitive information.
+ Ensure the availability and functionality of your network resources.
+ Improve your overall cyber resilience and make your network a harder target for attackers.

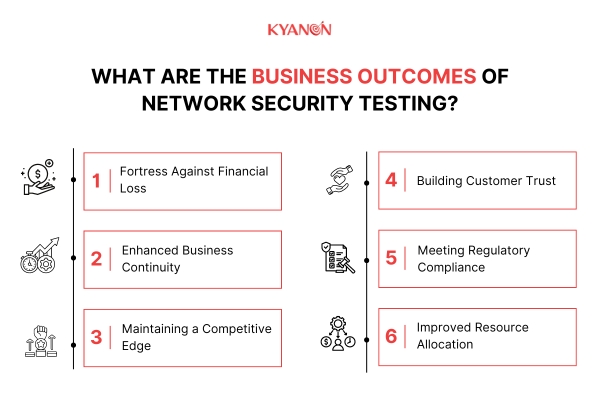
5. What are the business outcomes of Network Security Testing?
In today’s digital world, a secure network is the backbone of any successful business. Network security testing acts as a powerful tool for identifying and addressing vulnerabilities in your network infrastructure, leading to a range of positive business outcomes:
- Fortress Against Financial Loss: Data breaches can be crippling, leading to hefty fines, lawsuits, and reputational damage. Network security testing proactively identifies weaknesses that attackers might exploit, preventing these costly incidents and safeguarding your bottom line.
- Enhanced Business Continuity: Cyberattacks can disrupt network operations, leading to downtime and lost productivity. By ensuring your network is secure, you minimize the risk of disruptions, allowing your business to function smoothly and efficiently.
- Building Customer Trust: Customers entrust you with their sensitive data. Network security testing demonstrates your commitment to safeguarding that data, fostering trust and loyalty with your customers.
- Maintaining a Competitive Edge: Security breaches can damage your reputation and erode customer confidence. By prioritizing network security, you project a professional image and gain a competitive advantage in the marketplace.
- Meeting Regulatory Compliance: Many industries have regulations mandating specific security measures. Network security testing helps you ensure your network meets these compliance requirements, avoiding potential legal issues and fines.
- Improved Resource Allocation: Identifying vulnerabilities through network security testing allows you to prioritize security investments. You can allocate resources more effectively, focusing on the areas that pose the greatest risk.
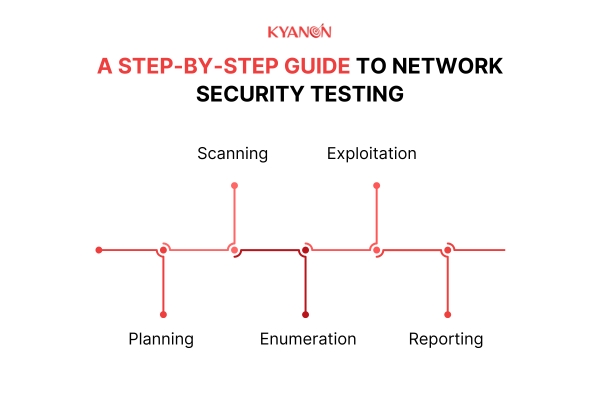
6. A Step-by-Step Guide to Network Security Testing
Network security testing involves simulating real-world attack scenarios to assess the strength of your defenses. The process generally includes the following steps:
- Planning: Define the scope, objectives, and methodologies for testing, and identify potential vulnerabilities.
- Scanning: Use automated tools to scan the network for weaknesses, open ports, and potential vulnerabilities.
- Enumeration: Actively probe the network to collect information about the target, such as IP addresses and system details.
- Exploitation: Ethical hackers attempt to exploit identified vulnerabilities to gain unauthorized access, highlighting weaknesses that require immediate attention.
- Reporting: Produce a comprehensive report detailing discovered vulnerabilities, their potential impact, and recommended remediation steps.
7. Conclusion
Network security testing is not just a precaution; it’s essential for protecting your business in today’s digital world. The benefits are undeniable: cost savings, comprehensive stakeholder protection, seamless business continuity, regulatory compliance, and increased trust among customers and clients.
With over 10 years of experience, Kyanon Digital is your trusted partner in securing your network. Our commitment to excellence is demonstrated by our 20+ business partners and our team of over 200 experts and professionals.
Contact us today for top-tier security testing services. Your business and stakeholders deserve nothing less than the best.


