Why enterprise low-code is a high-stakes decision in 2026?
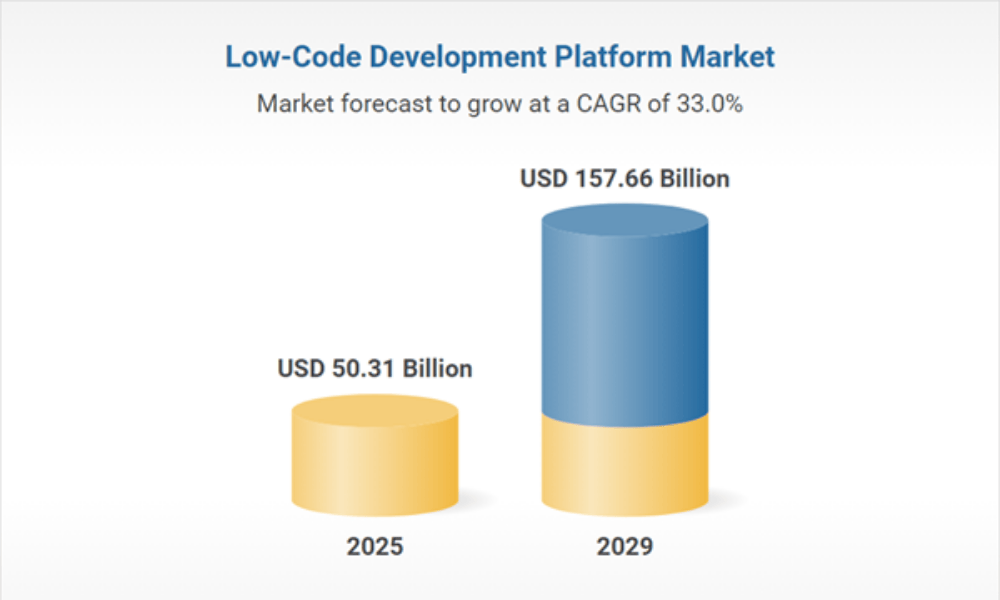
The global low-code development platform market is scaling rapidly, projected to grow from USD 50.31 billion in 2025 to over USD 157 billion by 2029 (Research and Markets), signaling that low-code has become a core enterprise delivery model rather than a tactical development option.
As adoption accelerates at enterprise scale, the conversation around low-code is shifting. C-suite leaders are no longer evaluating low-code based on speed of delivery alone, but on governance, scalability, security, and long-term total cost of ownership (TCO). What was once an experimentation layer is now treated as a strategic architecture decision with direct implications for risk, compliance, and operational resilience.
This shift is further amplified by agentic AI embedded in low-code platforms, which increases development velocity while introducing new enterprise risks, including AI-generated logic that is difficult to audit, invisible system dependencies, and widening governance gaps between business-led development and enterprise standards.
In this blog, Kyanon Digital highlights the top challenges of enterprise low-code that C-suite leaders must evaluate before scaling adoption across their organizations.
Further reading:
- Low-code/No-code Application Development
- What Are The Popular Enterprise Low-code Platforms?
- Top 5 Reasons Why Companies Should Go For Low-Code Development
- How To Choose The Right Low-code Development Platforms
What “enterprise low-code” really means now
Enterprise low-code refers to governed application platforms designed for large organizations that support accelerated application development while meeting enterprise needs for security, compliance, integration, and long-term maintainability.
According to Gartner, enterprise low-code application platforms (LCAPs) are software platforms that streamline the development and maintenance of applications using model-driven tools and prebuilt components across the full application lifecycle, making them suitable for mission-critical and large-scale use cases.
Unlike no-code tools, which are optimized for simplicity and business users, and traditional low-code platforms that emphasize rapid delivery, enterprise low-code platforms provide governance, extensibility, and risk controls necessary for cross-department deployment, enterprise integrations, and regulated environments.
Quick comparison table
|
Category |
Primary goal | Enterprise risk |
|
No-code |
Ease for individuals |
Limited governance and control |
|
Low-code |
Speed for teams |
Partial scalability and customization |
| Enterprise low-code | Governed, scalable delivery | Architecture, compliance, and TCO demands |
Why enterprise low-code becomes risky at scale
Enterprise low-code delivers speed and standardization in early adoption, but new risks emerge once platforms scale across departments, regions, and regulated environments.
As low-code shifts from isolated use cases to enterprise-wide deployment, it begins to interact directly with:
- Enterprise architecture standards
- Regulatory and compliance requirements
- Legacy ERP and core data systems
- Long-term cost, security, and operating models
At this stage, enterprise low-code no longer behaves like a development shortcut. It functions as enterprise infrastructure, where weaknesses in governance, integration, and cost control become structural rather than tactical issues.
This explains a common enterprise pattern:
- Early pilots succeed with minimal friction
- Expansion across teams exposes governance gaps and integration complexity
- AI-assisted low-code accelerates delivery while increasing accountability and audit pressure
In practice, the biggest challenges of enterprise low-code appear not because the technology fails, but because it succeeds and scales faster than enterprise controls can adapt. Understanding this transition is critical before evaluating low-code platforms, vendors, or implementation partners.
Transform your ideas into reality with our services. Get started today!
Our team will contact you within 24 hours.
Top 10 core challenges of enterprise low-code
Quick overview table
|
Challenge |
Strategic risk for business |
|
AI-driven shadow IT |
Loss of governance, security exposure, and unmanaged apps |
|
Hidden technical debt |
Long-term rigidity, blocked modernization |
|
Scalability ceiling |
Performance failures under enterprise load |
|
Runtime security gaps |
Data leaks, access violations, API exposure |
|
Brand & UX constraints |
Commoditized experience, weak differentiation |
|
Platform lock-in |
High exit costs, vendor dependency |
|
Hidden TCO |
Budget volatility, cost overruns |
|
Data sovereignty risk |
Regulatory exposure, cross-border data violations |
|
SDLC & DevOps gaps |
Release risk, weak reliability, poor visibility |
|
AI auditability |
Unexplainable decisions, regulatory risk |
AI-driven shadow IT 2.0 & operating model breakdown
AI-powered low-code enables business users to build apps faster than enterprise governance can control, creating unmanaged systems, security exposure, and accountability gaps.
Key signals
- The 4:1 ratio: Gartner predicts that by 2026, citizen developers will outnumber professional developers four to one, leading to a “governance gap” where 80% of low-code users operate outside formal IT oversight.
- Orphaned logic: Mission-critical workflows built by non-IT staff often lack documentation, becoming unmaintainable “black boxes” when the original creator leaves the company.
Business impact:
- Compliance penalties: Non-vetted apps frequently violate regional data laws like Vietnam’s Decree 13 or Singapore’s PDPA, leading to fines of up to 5% of global revenue.
- Data leakage: IBM reports that the average cost of a data breach has risen to $4.4 million globally, often triggered by unapproved AI tools sharing sensitive IP with public models.
Best practices for business:

- Establish a CoE: Create a low-code Center of Excellence to provide pre-approved templates and security guardrails.
|
Governance pillar |
Enterprise action |
|
App categorization |
Rank apps by risk (bronze, silver, gold). |
|
Federated identity |
Mandatory SSO (Okta/Azure AD) for all apps. |
| Automated guardrails |
Use DLP (data loss prevention) triggers. |
- Tiered risk labeling: Classify every app as “Bronze” (internal/low-risk) to “Gold” (customer-facing/high-risk) with mandatory IT sign-off for Gold-tier tools.
Hidden technical debt & enterprise architecture rigidity
Low-code abstraction hides architectural complexity, creating long-term technical debt that blocks modernization, upgrades, and future platform migration.
Accenture’s 2025 Digital Core report estimates USD 2.41 trillion in annual U.S. technical debt impact and USD 1.52 trillion needed for remediation.
While low-code accelerates initial delivery, it often hides architectural flaws behind proprietary visual layers. At enterprise scale, this creates “walled gardens” where applications become too rigid to refactor or migrate, eventually slowing down the very innovation they were meant to spark.
Key signals
- The quality crisis: Gartner warns that by 2026, AI-generated “prompt-to-app” code will increase software defects by 2500% if architectural checkpoints are bypassed.
- “Visual spaghetti”: Over-customizing visual workflows leads to complex, hard-to-read logic maps that are more difficult to debug than traditional codebases.
- Version control gaps: Standard CI/CD pipelines often struggle with proprietary low-code file formats, hindering multi-region team collaboration.
- Metadata bloat: Heavy platform overhead can lead to performance lag in high-concurrency scenarios.
- The “wrapper” trap: Over-reliance on custom JavaScript/CSS “wrappers” to bypass platform limits creates unmanaged security holes.
Business impact
- Diminishing ROI: Maintenance “interest” often outweighs initial speed savings within 3 years.
- Execution risk: Difficulty adapting to local regulations (like Singapore’s PDPA) due to platform constraints.
- Modernization walls: High technical debt consumes up to 42% of a developer’s weekly productivity, effectively halting innovation cycles (Stripe).
The best practice approach
To maintain agility, C-suite leaders should implement “architectural guardrails”:

- Standardized extensibility governance: Define strictly where custom code is allowed.
- Platform audits: Conduct bi-annual reviews of metadata health and dependency trees.
- Modular decoupling: Use low-code for the UI layer while keeping mission-critical logic in portable microservices to ensure long-term sovereignty.
Scalability & performance ceiling at enterprise load
Many low-code platforms struggle under enterprise-level concurrency, regional traffic, and AI workloads, exposing performance limits only after adoption scales.
At enterprise scale, the abstraction layer that enables “drag-and-drop” development often introduces a “performance tax” that becomes visible only during peak loads or complex data processing tasks.
Key signals
- N+1″ query problems: Research from OutSystems indicates that poorly architected low-code apps face exponential latency increases once data sets exceed 100,000 records due to inefficient visual query builders.
- Shared environment throttling: Multi-tenant cloud platforms may throttle your application’s IOPS (Input/Output Operations) if a neighboring “tenant” on the same server experiences a traffic spike.
- Cold start latency: AI-generated workflows often require high initialization times, causing frustrating “spinning wheels” for enterprise end-users (ArXiv).
Business impact
- Revenue leakage: Slow internal tools, such as lagging CRM or POS, directly decrease employee productivity and customer transaction speeds.
- Reliability risk: System crashes during peak periods, such as 11.11 or regional holiday sales, due to an inability to scale horizontally on demand.
- Unplanned scaling costs: Reaching a performance limit often forces an emergency (and unbudgeted) move to a “premium tier” that can triple licensing costs.
The best practice approach
C-suite leaders must ensure that “speed to market” does not sacrifice “speed of use.” Strategic decoupling is the primary solution for high-performance requirements.

|
Strategy |
Actionable step |
|
Backend decoupling |
Move heavy logic to AWS/Azure/GCP. |
|
Edge caching |
Use CDNs for regional APAC users. |
| Load testing |
Mandate “peak load” tests before go-live. |
Runtime security, data flow & access control gaps
Low-code speed often outpaces security oversight, creating risks in access control, API exposure, secrets handling, and unmonitored data movement.
While the underlying platform infrastructure is usually secure, the “logic” built on top of it often is not. In a low-code environment, a non-technical user can inadvertently create a public-facing API or an insecure data connection with a single click.
Key signals
- “Broken” access control: Citizen developers often grant “Admin” rights to too many users to ensure the app “just works,” violating the principle of least privilege.
- Insecure API endpoints: Many platforms allow users to expose database tables as public REST APIs without proper authentication or rate limiting.
- Lack of secrets management: API keys for regional services are often stored in plain text within the low-code application logic.
- Shadow data egress: Native connectors can send enterprise data to unapproved personal storage accounts without triggering standard data loss prevention (DLP) alerts.
Business impact
- Intellectual property theft: Unauthorized data export via unmonitored low-code connectors can lead to the loss of proprietary business logic or customer lists.
- Brand damage: Publicized data leaks caused by misconfigured “anonymous access” settings can destroy consumer trust in highly competitive markets like Singapore.
- Regulatory penalties: Non-compliance with data protection laws (PDPA/GDPR) due to an inability to prove who accessed what data within a low-code tool.
The best practice approach
C-suite leaders must transition from manual security reviews to automated guardrails within the platform itself.

|
Strategic pillar |
Actionable step |
Business benefit |
|
Identity management |
Mandatory SSO/MFA for all app access. |
Reduces unauthorized entry points. |
|
Governance policy |
Disable “custom connectors” for non-IT users. |
Prevents unvetted data pipelines. |
|
Lifecycle control |
Automated staging-to-production approvals. | Ensures IT oversight on every release. |
Brand, UX & differentiation constraints
Template-driven low-code platforms limit customization, forcing enterprises to compromise on user experience, localization, and brand differentiation.
Key signals
- “Visual spaghetti”: Forcing complex logic into drag-and-drop editors creates workflows that are harder to debug and audit than traditional code.
- Component fragmentation: When templates fail, developers create “custom wrappers” (JS/CSS) that bypass platform security and performance checks.
- Localization gaps: Global templates often lack native support for regional APAC requirements, such as specific tax engines or government digital signatures.
Business impact
- Compromised UX: Standardized interfaces can lead to “platform fatigue,” reducing internal productivity and external brand value.
- Shadow pro-code costs: High-priced senior developers are often pulled in to “fix” template limitations, negating the cost-savings intended by using a low-code platform.
- Innovation stagnation: Business processes are forced to adapt to the tool’s limits rather than the customer’s needs.
The best practice approach
C-suite leaders should adopt a “platform + pro code” strategy to prevent functional dead-ends and maintain brand integrity.
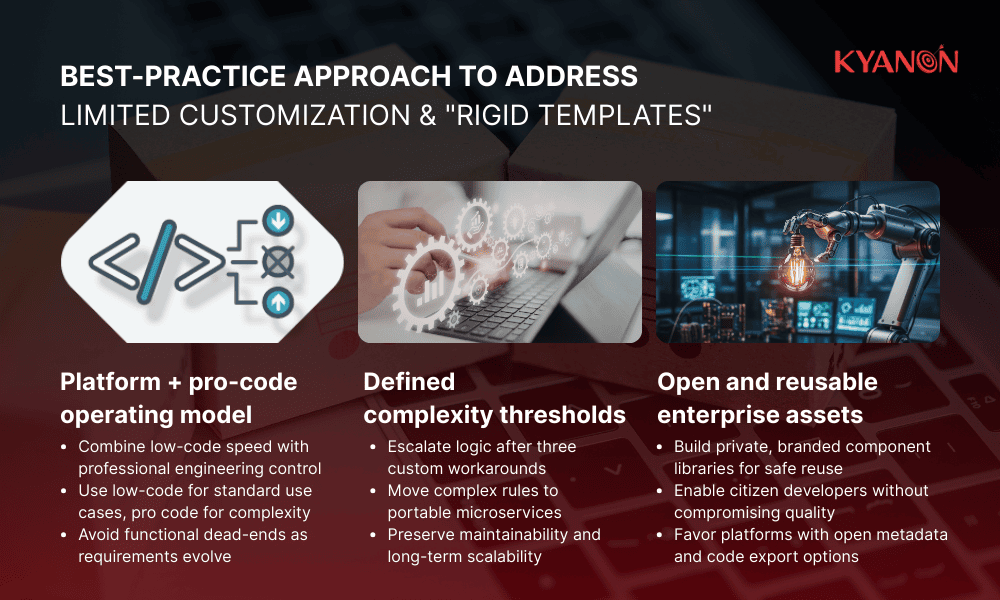
- Define “complexity thresholds”: If a requirement needs more than three “custom workarounds,” move the logic to a portable microservice.
- Build private component libraries: Have pro-developers create pre-approved, branded widgets that citizen developers can safely reuse.
- Prioritize open metadata: Select vendors that allow for underlying code export if the visual editor becomes insufficient for future scaling.
Proprietary platform lock-in & exit risk
Proprietary low-code languages, metadata, and connectors create high exit costs and long-term dependency on a single vendor ecosystem.
Key signals
- The migration barrier: 62% of IT decision-makers cite vendor lock-in as their top concern for 2026, as proprietary formats prevent simple “lift-and-shift” migrations to the cloud (BCG).
- High exit costs: Rebuilding a complex enterprise low-code app while being tied to a proprietary platform often leads to costly migration and reconfiguration when switching providers because data, APIs, and application logic are not portable.
Business impact:
- Vendor lock-in drives high exit costs: Proprietary platforms make apps, data, and workflows hard to migrate, turning platform switching into a costly rebuild exercise.
- Portability limits reduce business agility: When logic and integrations are tightly coupled to a low-code vendor, enterprises lose flexibility to respond to pricing changes or strategic shifts.
- Lock-in becomes a long-term financial risk: Analysts warn that platform dependency weakens negotiating power and increases long-term technology costs.
The best practice approach
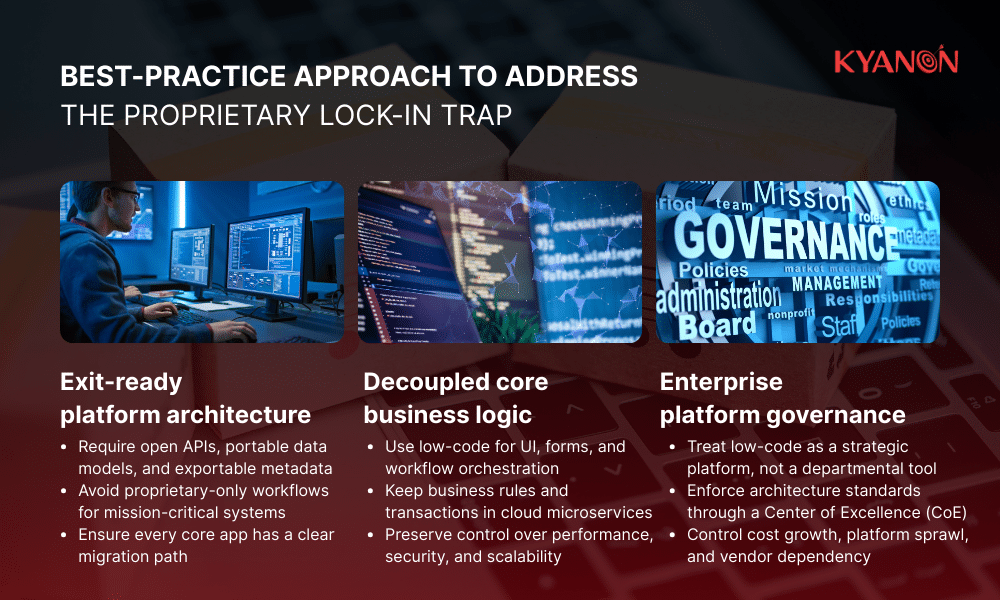
- Design for exit from day one: Require open APIs, portable data models, and exportable metadata so critical apps are never trapped inside a single vendor platform.
- Decouple core business logic from low-code: Use low-code for UI and workflows, but keep mission-critical logic in cloud microservices to preserve long-term control and scalability.
- Govern low-code as a strategic platform, not a tool: Enforce architecture standards, platform audits, and cost controls through a Center of Excellence to prevent lock-in and bill shock.
Hidden total cost of ownership (TCO)
Consumption-based pricing, environment sprawl, and long-term maintenance quietly inflate low-code costs beyond initial project budgets.
Key signals
- Consumption or user-based pricing increases sharply as adoption grows
- Multiple environments (dev/stage/prod) incur repeated licensing fees
- Custom workarounds and extensions drive vendor support costs
- Platform upgrades trigger unplanned testing and rework overhead
- Shadow IT projects accumulate without centralized cost visibility
Business impacts
- Budget volatility: Early low-code projects often show cost savings, but total spend grows unpredictably as usage scales across departments.
- Long-term spend creep: Many cloud services follow a pay-as-you-go pricing model, where costs are driven by usage (compute, data, storage). Without disciplined cost governance, bills can escalate rapidly, a pattern that contributes to the TCO in enterprise low-code deployments (IBM).
- Opportunity cost: Money tied up in platform costs limits investment in strategic capabilities like AI integration, data platforms, or security enhancements.
The best practice approach
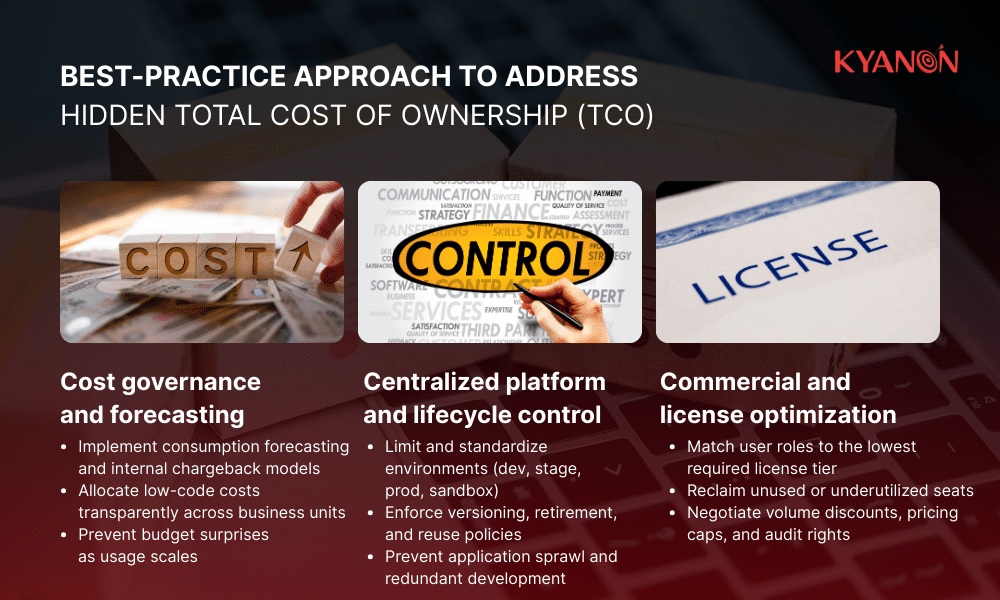
- Adopt consumption forecasting and chargeback models: Establish forecasting and internal chargeback to anticipate and allocate low-code costs across business units.
- Centralize environment management: Limit the number of dedicated environments (dev, stage, prod) and enforce cost controls on sandbox or proof-of-concept instances.
- Standardize lifecycle policies: Use policies for versioning, retirement, and reuse to avoid sprawl and redundant development.
- Optimize license usage: Match user roles to the lowest tier of access required and reclaim unused or underutilized seats.
- Track true TCO with integrated cost dashboards: Combine platform, infrastructure, support, and maintenance costs in a single dashboard to inform executive decisions.
- Negotiate long-term commercial terms with vendors: Secure volume discounts, predictable pricing caps, and rights for audit and usage reporting.
Data sovereignty & regional compliance risk
Global low-code SaaS platforms often conflict with local data protection and residency laws across APAC, Singapore, and Vietnam, creating regulatory and legal exposure for enterprises.
Key signals
- Platform data hosted only in foreign regions (US, EU)
- Limited control over physical data location
- Inability to restrict cross-border data access
- Vendor-controlled backup and disaster recovery regions
- No clear audit trail for data movement
Business impact
- Regulatory exposure: Risk of fines, audits, and operational restrictions under local data laws
- Market access risk: Some industries and public-sector contracts require in-country data hosting
- Legal liability: Inability to prove compliance during regulatory investigations
- Trust erosion: Customers and partners expect strong data protection guarantees
The best practice approach

- Regional data control strategy: Select platforms with in-country or regional data centers and require contractual data-residency guarantees to meet local compliance requirements.
- Compliance-by-design architecture: Map and classify all data flows and automatically enforce region-specific compliance policies across every low-code application.
- Sovereign data operating model: Keep regulated data in private or hybrid cloud while using low-code only for UI and orchestration via secure APIs.
Enterprise SDLC & operational maturity gaps
Many low-code platforms do not fully align with enterprise software delivery standards, creating gaps in testing, release control, observability, and incident accountability.
Key signals
- Manual deployment and rollback processes
- Limited integration with Git, Jenkins, GitLab, and Azure DevOps
- No automated regression testing
- Black-box runtime monitoring
- Vendor-controlled upgrade schedules
Business impact
- Release risk: Higher probability of production failures
- Operational fragility: Slower incident response and root-cause analysis
- SLA exposure: Reduced reliability for customer-facing systems
- Audit gaps: Incomplete change and release traceability
The best practice approach
- Enterprise-grade delivery pipelines: Integrate low-code into standard CI/CD tooling with automated testing and version control to ensure safe, repeatable releases.
- Release and change governance: Enforce staging-to-production approvals, change workflows, and rollback procedures to protect business-critical systems.
- Full-stack observability: Connect low-code platforms to enterprise monitoring to track performance, errors, and usage with executive-level visibility.
AI logic explainability & auditability
AI-generated workflows and decisions inside low-code platforms often lack transparency, traceability, and regulatory audit readiness.
Key signals
- No version control for AI models or prompts
- No explanation of decision logic
- No audit logs for AI-driven actions
- Limited control over training data
- Vendor-managed model updates
Business impact
- Regulatory exposure: Inability to defend automated decisions
- Legal risk: Challenges in credit, hiring, pricing, or fraud decisions
- Trust erosion: Customers demand transparency and accountability
- Brand damage: Public backlash from opaque AI outcomes
The best practice approach

- Explainable AI is now a compliance requirement: Enterprises must be able to explain how AI-driven decisions are made, especially in regulated areas like finance, hiring, healthcare, and public services.
- Ungoverned AI creates legal and reputational risk: Black-box AI workflows without version control or approval expose businesses to audit failure, regulatory penalties, and loss of customer trust.
- Audit-ready AI protects enterprise accountability: Full logging, decision traceability, and historical records are essential for regulatory reporting and executive oversight.
Case study: Kyanon Digital modernizes Temasek Life Sciences Laboratory’s intranet with low-code solutions
Kyanon Digital modernizes Temasek Life Sciences Laboratory’s intranet with low-code solutions.
Temasek Life Sciences Laboratory (TLL) is a leading research institute in Singapore specializing in biotechnology. To improve internal collaboration and efficiency, TLL needed to upgrade its legacy intranet system.
Challenge
TLL faced outdated technology, limited functionalities, and a lack of internal IT capacity. The organization needed a scalable, secure, and modernized intranet to support growing operational demands.
Solution
- Kyanon Digital deployed a dedicated engineering team and implemented low-code technologies to accelerate development and modernization.
- Migrated legacy modules to a low-code platform for faster updates
- Enhanced performance with proactive monitoring and structured governance
- Added new features to improve usability and workflow automation
Results
- Faster feature deployment with minimal coding
- Improved system stability and user experience
- Streamlined operations and easier scalability
Services & technologies
Services: Low-code development, dedicated team, IT outsourcing
Technologies: PHP, Outsystems
The 2026 decision-maker’s checklist for enterprise low-code
In 2026, choosing an enterprise low-code platform is a strategic architecture decision that directly impacts governance, compliance, scalability, and long-term total cost of ownership.
Executive audit checklist
|
Audit criteria |
What business leaders should verify |
Why it matters |
|
Governance aligned with enterprise architecture |
Centralized control, security policies, identity, and role management |
Prevents shadow IT, audit gaps, and compliance risk |
|
Data portability & exit strategy |
Open data formats, documented migration path, no vendor-only dependencies |
Protects long-term flexibility and vendor independence |
|
Logic inspection & versioning |
Ability to review, approve, and rollback workflows and rules |
Ensures auditability and operational control |
|
AI-generated logic auditability |
Explainable AI decisions, full logging, traceable automation |
Reduces regulatory and legal exposure |
|
Integration depth with core systems |
Native ERP, finance, HR, CRM, and data platform connectivity |
Enables real enterprise value creation |
|
Licensing transparency & long-term TCO |
Predictable pricing, clear scaling model, no hidden API or usage fees |
Protects budget stability as adoption grows |
|
Execution vs. vision alignment |
Proven enterprise deployments, roadmap aligned to large-scale needs |
Ensures reliability before innovation |
Conclusion: Moving beyond the hype of low-code
It is necessary to evaluate how long it takes a business user, and if needed, a developer, to speed up using the platform for their expected business goal.
Keep in mind that employee turnover and a lack of a desire amongst employees to be specialized in a specific, limited platform will make platforms with a long training and onboarding stage even more expensive to operate over time. If there are a cadre of consultants and developers who are selling implementations of the platform, it absolutely is not as easy as advertised to use.
It is important to understand what an enterprise low-code platform can actually accomplish and the resources it requires. Assess whether, once this is considered, it is beneficial to have in the tech stack, and, if so, for what specific business goals.
We hope you enjoy this article. If you are finding a reliable provider to help you build an enterprise application with a low-code platform, please do not hesitate to contact Kyanon Digital via email. Our experts will help you make the appropriate choice.
Get the Vietnam Software Outsourcing Pricing Guide 2025
Your shortcut to Vietnam’s outsourcing costs and key market insights.

Why work with Kyanon Digital?
- Expertise Trusted by Fortune 500 Clients
With deep experience serving Fortune 500 companies, we deliver tailored, high-impact solutions that meet the unique demands of global enterprises. - A World-Class IT Team
Our 500+ IT experts—spanning consulting, project management, technical architecture, software engineering, QA, DevOps, and AI/ML—are committed to excellence in every project. - Quality at the Core
Certified under ISO 9001, our quality-first approach guarantees precision, reliability, and continuous improvement. - Uncompromising Security
ISO 27001-certified, we integrate robust security into every process, leveraging advanced technologies to protect your data against evolving threats.


















